This is the write up for Pasteurize Google CTF 2020 challenge from the perspective of someone who does not routinely do CTFs. A friend of mine teamed up with me and even though we did not go that far, we had fun and learned something. Challenge description In this challenge, we get a URL: https://pasteurize.web.ctfcompetition.com/ and a description that says: This doesn’t look secure. I wouldn’t put even the littlest secret in here. My source tells me that third parties might have implanted it with their little treats already. Can you prove me right? On this website, we can...
Continue reading...Setting up XDebug for PHPStorm on Windows & WSL2
In this post, I’m going to go over my short journey to setup my PHP development environment on Windows 10. I will tell you how to setup PHPStorm to debug PHP applications using XDebug and PHP setup over Ubuntu 18.04 LTS on WSL2. I would like to work against the latest version of PHP and compile it myself. At the same time, setting up extensions and compiling PHP itself on windows is not a very straightforward task as far as I know. The plan is to have the development environment run from Linux (WSL2) while the IDE, which is PHPStorm...
Continue reading...Getting started with PHP-CFG
PHP-CFG is PHP project developed by Anthony Ferrara. It uses PHP-Parser to generate the AST from the PHP code. Then transforms this into another intermediate representation in the form of a control flow graph. This enables us an easy way to traverse this graph and reason about the execution of the underlying PHP code. Getting started To get started, you’d need to know some basic compiler concepts. The audience of this post are people from a variety of backgrounds so I’ll try to cover as much as possible. If some concepts don’t make sense through out the text, it is...
Continue reading...Shrinking a LaTeX paper to fit under the page limits
As PhD students or grant writers, I’m sure we have all been there. You need to squeeze in two more paragraphs into the text and stay under the 12 page limits. Sometimes you can throw away another paragraph that is not so necessary. Other times you can rephrase multiple sentences and save several lines. Shrinking figures is always an option. You know what’s worse? Resubmitting a paper to a conference with a less forgiving template in terms of space, or just a smaller page limit. Once the idea is shaped and the text is written, it is indeed harder to...
Continue reading...PHP builtin functions usage statistics
I was working on a project which required implementation of PHP builtin functions. To understand the scope of the project and its implementation effort I thought it is a good idea to get an estimate of the total number of these functions, and also, how frequently they are used among popular PHP applications. This would give me a rough idea of how many functions I need to implement myself. At the same time, the results can be leveraged to get insight into debloating effectiveness for these applications. Which is something that I’ve been working on for over a year now....
Continue reading...Evaluating the Effectiveness of Miner Blocker Browser Extensions
JavaScript crypto miners have been around for quite a while. Monero (XMR), the crypto currency mined by these scripts was released in April 2014. As shown in the following figure, the increase in price of Bitcoin was coupled with increase in price of Ethereum and Monero. This jump led to these in browser miners being over emphasized in the media. Advertisements being replaced by miners Website administrators started including miner scripts in their websites. The more the user stays on the website, the more Monero mined. Coinhive review: Embeddable JavaScript Crypto Miner – 3 days in [1] shows that using...
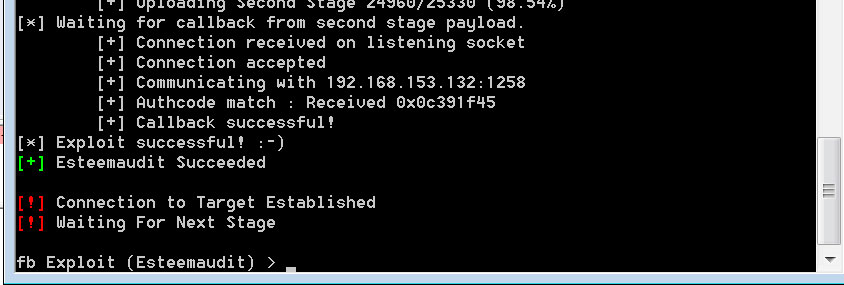
Continue reading...Shadowbrokers’ Leaks, Next Versions of WannaCry and Adylkuzz on the Rise
Introduction During the past couple of weeks, we have seen a rise in public abuse of Shadowbrokers’ leaked exploits allegedly used by the NSA, a handful of these exploits target windows operating system and gives attackers the ability to reliably penetrate into windows boxes! Eternalblue is the name of the exploit that targeted SMB 445 port on windows operating systems that gave you RCE, it was patched by Microsoft a couple of days before the leak but many systems were left vulnerable over the internet, in addition to that, windows XP and 2003 which are no longer supported by Microsoft...
Continue reading...Analysis of a Scam: Fake Telegram Client (BlackGram)
I’m officially contributing to telescam.ir project where we analyze the growing trend of android malware and scam campaigns spreading via Telegram messenger in Iran. Since Telegram is the dominant messaging application used by Iranians, scammers have built their tools and services on top of this infrastructure. We have observed scam campaigns where they take your money but don’t deliver the service they promised and we have also observed the case where various social engineering techniques are used to get access to client contacts or add them to their advertisement channels. These guys are operating channels with 170,000+ members, and using...
Continue reading...Never Trust Untrusted SSL Certificates, XSS in Certcc SSLCheck subdomain
In this blog post I’m going to discuss the XSS vulnerability that I found in sslcheck.certcc.ir. Certcc has developed its own SSL configuration assessment service (like SSLLabs.com). The good point about this is that websites that are only reachable from Iran’s IP addresses can be tested using this service. I was playing around with this website to see how it works in contrast to SSLLabs.com, I found out that it gives you much more options like entering ip addresses, testing custom ports and also testing services that work with SSL like SMTP, IMAP and POP3. There was a part of...
Continue reading...Easy Money, As Simple As An Android Scam!
The story – Smelly Smelly apk One of my colleagues came to me with an apk (Android application), he said he can’t make it work on his Genymotion emulator but he’s 100% certain it’s an Iranian malware. Based on his observation the guy behind this application was spending more than 500$ daily to spread this app on Telegram messenger public channels, he was basically paying channel administrators with huge number of members to advertise and spread his application. A non-exhaustive list of channels observed by us is provided at the end of this post (note that channel moderators remove the...
Continue reading...